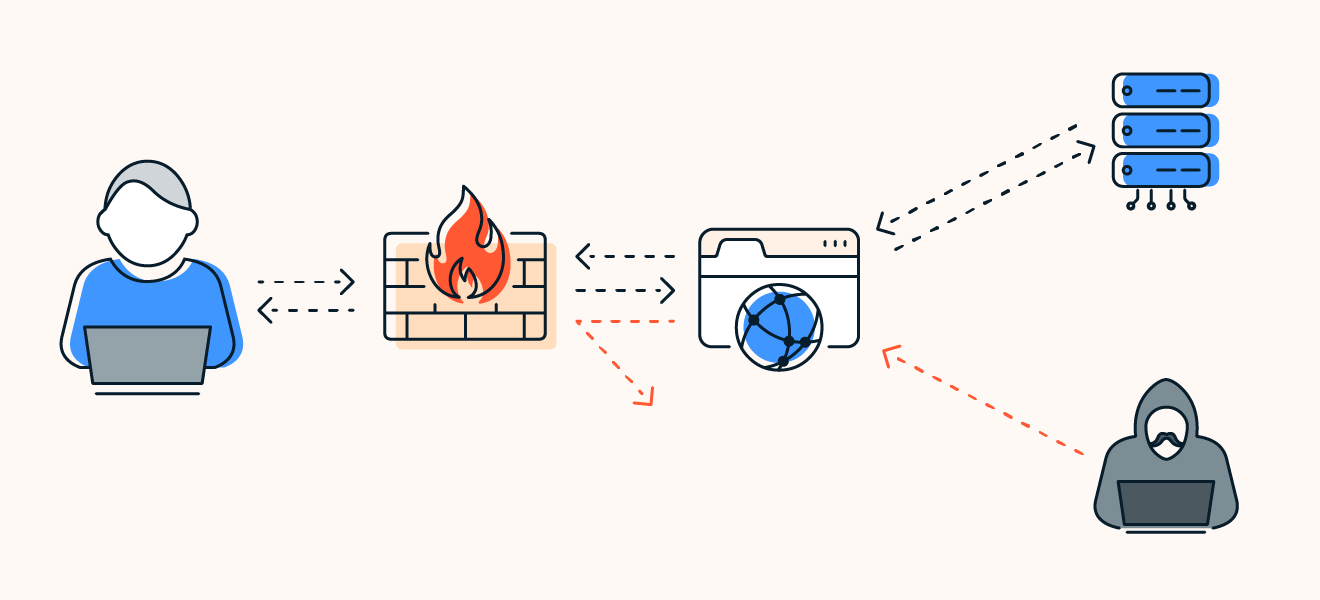
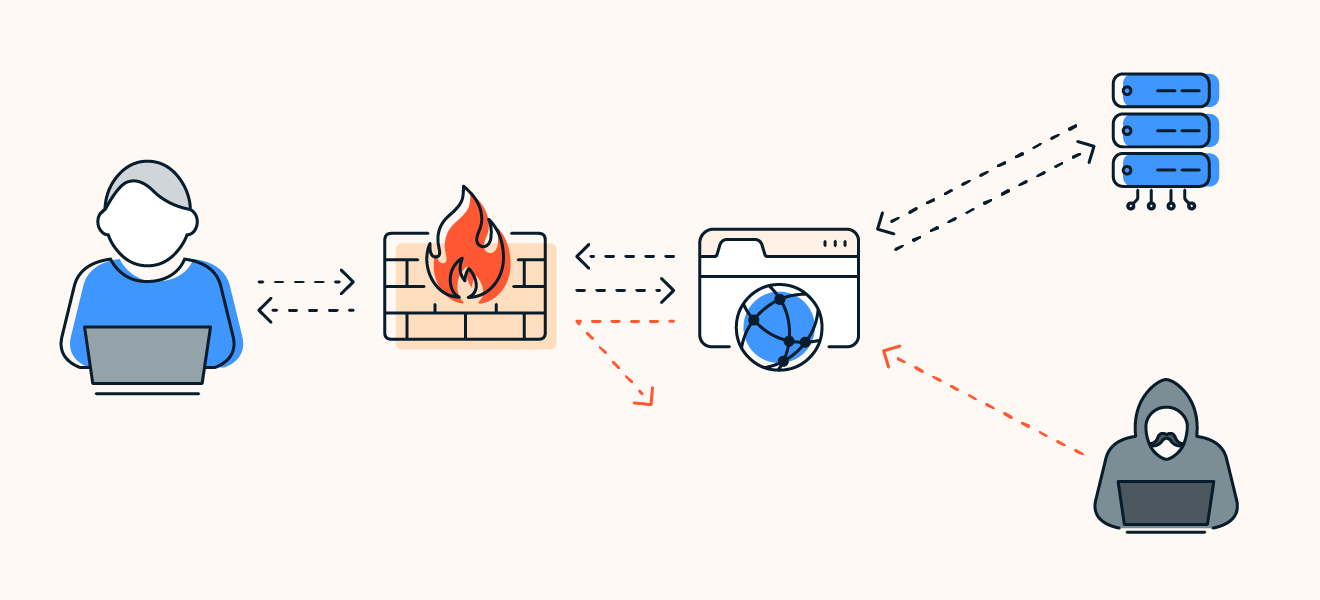
Understanding Firewalls
In the realm of network security, firewalls play a critical role in protecting your digital assets from unauthorized access and cyber threats. As the first line of defense against potential attacks, understanding how firewalls work and why they are essential is crucial for maintaining a secure network environment. This blog post provides an in-depth look at firewalls, including their functions, types, and the reasons why they are indispensable for network security.
What is a Firewall?
A firewall is a network security device or software that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and untrusted external networks, such as the internet. Firewalls help prevent unauthorized access, block malicious traffic, and protect sensitive information from potential threats.
How Firewalls Work
1. Traffic Filtering
Firewalls analyze network traffic to determine whether it should be allowed or blocked based on predefined security rules. This filtering process involves examining data packets and assessing their source, destination, and content. Traffic that meets the criteria for security is permitted, while traffic that does not is blocked or flagged for further inspection.
2. Packet Inspection
Firewalls perform packet inspection to scrutinize data packets for potential threats. There are two primary types of packet inspection:
- Basic Packet Filtering: Examines the packet headers, such as source and destination IP addresses and port numbers, to make filtering decisions. It does not analyze the packet content, making it less thorough but faster.
- Deep Packet Inspection (DPI): Analyzes both the header and content of packets to detect and block more sophisticated threats, such as malware and intrusions. DPI provides more comprehensive security but may introduce additional processing overhead.
3. Stateful Inspection
Stateful inspection, also known as dynamic packet filtering, tracks the state of active connections and uses this information to determine whether a packet is part of an established connection or a new one. This approach enhances security by ensuring that only legitimate traffic associated with active connections is allowed.
4. Proxy Services
Some firewalls offer proxy services, which act as intermediaries between clients and servers. A proxy firewall intercepts requests from clients, forwards them to the intended server, and then returns the server’s response to the client. This approach provides an additional layer of security by hiding the internal network and filtering requests before they reach the server.
Types of Firewalls
1. Packet-Filtering Firewalls
Packet-filtering firewalls operate at the network layer and examine packets based on predefined rules related to IP addresses, ports, and protocols. They are simple and efficient but may not provide advanced threat protection.
2. Stateful Inspection Firewalls
Stateful inspection firewalls maintain a table of active connections and make filtering decisions based on the state of each connection. They offer enhanced security by ensuring that only valid, established connections are allowed.
3. Proxy Firewalls
Proxy firewalls act as intermediaries between clients and servers, providing additional security by masking internal network addresses and filtering requests. They are effective at blocking unwanted content and applications.
4. Next-Generation Firewalls (NGFWs)
Next-Generation Firewalls (NGFWs) combine traditional firewall capabilities with advanced features such as intrusion prevention, application awareness, and threat intelligence. NGFWs provide comprehensive protection against modern threats and offer more granular control over network traffic.
5. Unified Threat Management (UTM) Firewalls
Unified Threat Management (UTM) firewalls integrate multiple security functions, including firewall protection, antivirus, anti-spam, and intrusion prevention, into a single device. UTMs offer a holistic approach to network security by consolidating various security features.
Why You Need a Firewall
1. Protects Against Unauthorized Access
Firewalls help prevent unauthorized users and malicious entities from gaining access to your network and sensitive information. By filtering traffic and enforcing access control policies, firewalls safeguard your network from potential intrusions.
2. Blocks Malicious Traffic
Firewalls block harmful traffic, such as malware, ransomware, and other malicious software, from entering your network. They use threat intelligence and signature-based detection to identify and prevent known threats.
3. Ensures Network Security Compliance
Many industry regulations and standards, such as GDPR, HIPAA, and PCI-DSS, require organizations to implement firewalls and other security measures to protect sensitive data. Using firewalls helps ensure compliance with these regulatory requirements.
4. Monitors Network Activity
Firewalls provide visibility into network activity by logging and monitoring traffic patterns. This monitoring helps detect unusual or suspicious behavior, allowing you to respond quickly to potential threats.
5. Controls Access to Applications
Firewalls can enforce application-level controls, restricting access to specific applications and services based on user roles or policies. This control helps prevent unauthorized use and reduces the risk of security breaches.
Best Practices for Firewall Management
1. Regularly Update Firewall Rules
Regularly review and update firewall rules to ensure they align with your organization’s security policies and adapt to evolving threats. Remove outdated or unnecessary rules to reduce potential vulnerabilities.
2. Monitor and Analyze Logs
Continuously monitor and analyze firewall logs to identify and investigate potential security incidents. Use log analysis tools to gain insights into network traffic and detect anomalies.
3. Implement Layered Security
Combine firewalls with other security measures, such as antivirus software, intrusion detection systems, and encryption, to create a multi-layered defense strategy. Layered security provides comprehensive protection against various threats.
4. Conduct Regular Security Audits
Perform regular security audits to assess the effectiveness of your firewall configuration and overall network security. Audits help identify weaknesses and ensure that your firewall is operating correctly.
5. Educate and Train Staff
Educate and train staff on firewall policies and best practices to ensure proper usage and management. Awareness and training help prevent accidental misconfigurations and enhance overall security.
Conclusion
Firewalls are a fundamental component of network security, providing essential protection against unauthorized access, malicious traffic, and cyber threats. By understanding how firewalls work, the different types available, and the reasons why they are crucial for safeguarding your network, you can make informed decisions about implementing and managing these critical security devices. Adopting best practices for firewall management and combining firewalls with other security measures will help ensure a robust defense against evolving threats in today’s digital landscape.